Windows操作系统在服务器上安装非常广泛,企业或个人经常安装的操作系统有Vhndows Server 2000、2003和2008等,这些操作系统的本身漏洞我们无法控制,但我们可以通过系统安全加固手段有效降低自己服务器被黑客入侵的几率。日前常见的加固手段主要包括账户设置、组策略设置、注册表设置、IPSec、服务设置等,本文主要讲如何通过编程方式操控组策略从而实现Windows操作系统的安全加固,下表为在组策略巾需要进行的相关配置。
密码复杂性要求:启用 最短密码长度: 8位
帐户策略 密码最长使用期限: 0天 密码最短使用期限: 0天
强制密码历史: 0个记住的密码
复位帐户锁定计数器: 5分钟 帐户锁定时间: 30分钟
帐户锁定策略
“复位帐户锁定阐值”5次
成功,失败:审核帐户登录事件、 审核帐户管理、审核日录服务访问、
审核登录事件、审核特权使用
审核策略 失败:审核对象访问
成功:审核策略更改、审核系统事件
无审核:审核过程追踪
通过终端服务拒绝登录:无
用户权限指派
通过终端服务允许登录: Administr ators组和remote desktop users组
交互式登录:不显示上次的用户名 启用
网络访问:不允许SAM帐户和共享的匿名枚举 启用
网络访问:不允许为网络身份验证储存凭证 启用
安全选项 网络访问:可匿名访问的共享 全部删除
网络访问:可匿名访问的命名管道 全部删除
网络访问:可远程访问的注册表路径 全部删除
帐户:重命名系统管理员帐户 重命名一个帐户
组策略与注册表的关系非常紧密,许多组策略中的设置可以通过修改注册表,然后用RefreshPolicy函数强制刷新组策略来实现(其实有些组策略修改的实质也正是修改注册表相关配置),例如上表巾的“不显示上次的用户名”和“不允许SAM帐户和共享的匿名枚举”等。但是有些组策略的设置无法通过注册表进行修改,例如上表巾的账户策略、账户锁定策略、审核策略和用户权限指派等。所以本文通过Kindows白带的secedit这个命令对组策略进行设置,主要用到的命令是secedit /configure /db FileName /cfg FileName/quiet.其巾/db后的文件名可任意取,一股以.sdb为后缀名,/cfg后的文件为我们需要配置的文件。该命令的其他语法和具体使用方法网上可以查到,这里不再赘述。 如何将表巾的组策略设置对应到配置文件巾,账户策略、账户锁定策略在配置文件巾的配置命令格式如何,这些我们可以参考Windows自带的配置文件模板,模板位于C:WINDOWS\Security\templates下。通常为inf格式文件。在配置文件中,分号代表注释符,其后可跟注释语句
..... :头部一些声明
[System Access]
blinimumPassvrordAge=0 :密码最短使用期限
MaximumPassvrordAge=-1 :密码最长使用期限,此处一1代表0.若写 0则会出错
blinimumPassrrordLength=8 :最短密码长度
PassvrordCoruplexity=1 :密码复杂性要求
PassvrordHistorySize:0 :强制密码历史
NerrAdministratorName=’testAdministr ator’:重命名系统管理员账户,名字可自己设定
LockoutBadCount=5 :账户锁定阀值
ResetLockoutCount=5 :复位账户锁定计数器
LockoutDuration=30 :账户锁定时间
[Event Audit]
:事件审计,0代表不审汁,1代表成功审计,2代表失败审计,3代表成功失败均审计
AuditSystemEvents=1 :系统事件成功
AuditObjectAccess:2 :对象访问失败
AuditPrivilegeUse=3 :特权使用成功失败
AuditPolicyChange=1 :策略改变成功
AuditAccountllanage=3 :账户管理成功失败
AuditProcessTracking=0 :过程追踪无审核
AuditDSAccess=3 :目录服务访问成功失败
AuditAccountLogon=3 ;账户登录成功失败
AuditLogonEvents=3 :登录事件成功失败
[Registry Values]
:这里的设置格式为path=Type,Value.其中常用的Type有:1代表REG- SZ.2代表REG EXPAND_SZ,3
代表REG_ BINARY,4代表REG_ DWORD.7代表REG HULTI_SZ
MACHINE\Softvrare \Xicr osoft VVindoWs\Curr entVer sion\Policies\Syst em\DontDisplayLastUserName=4
,1 :显示上次的用户名
lIACHINE\System\CurrentControlSet\Control\Lsa\DisableDomainCreds=4,1 :小允许为刚络身份验证
储存凭证
MACHINE\System\Current Contr olSet\Contr ol\Lsa\Restr ictAnonymou s=4,1 :小允许SAM帐户和共享
的匿名枚举
HACHINE\ Sys tem\Current Contr olSet\Contr ol\ SecurePipeServers\Winre g\Allorre dExact Paths \Uachine= 7, ,可远挫访问的注册表路径
MACHINE\Sys tem\Curr ent Contr olSet\Services \LanllanServer \Paramet ers \NullSes si onPipe s=7,
.可匿名访问的命名管道
MACHINE\Sys tem\Current Contr olSet\Services\LanManServer \Paramet ers\NullSes sionShare s=7,
.可匿名访问共享
.Privilege Rights]
SeRemoteInteractiveLogonRight=:*S-1-o-32-550,:*S-1-5-32-544 :通过终端服务允许登录
SeDenyRemoteInteractiveLogonRight= :通过终端服务拒绝登录
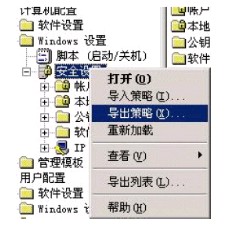
如果需要对其他的组策略进行设置,但是又不知道对应的修改项和值,可以采用以下的方法:首先,打开注册表,选择相应的项右击,点击“导出策略”,保存为1.inf,如图1所示:然后手工修改需要设置的项和值,再次选择“导出策略”,保存为2.inf:最后使用文本比较软件(如ucl.exe).将两者进行比对,不同之处就是刚才设置的值,找到之后就可以在配置文件中进行相应的设置。
下面我们编程实现组策略的设置,具体的思路是通过用户的选择设置组策略的配置文件,然后通过secedit命令将配置文件导入到组策略巾生效,最后清除产生的中间文件,核心代码如下:
CFile inf;
inf. Open (_T("c:\\czbank inf"),CFile::modeCreate CFile::modeWrite): //创建配置文件
char* str=":Unicode]\r\nLnicode3res\r\n-----------”: //具体配置信息此处略过
inf. Write (str, strlen (str)): //写入配置信息
if(用户的选择)(
char *str:-blinimumPasssrordAge:0\r\n……”:
inf. wrrite (str, strlen (str)): //根据用户选择写入配置信息
)
//重命名系统管理员用户名需要特殊处理
LpdateData (TRUE): //用户填写的用户名输入
if(adminName.Compare(_T(~))f_0){ //用户名为空则小处理
CString strName=_T(-NevrAdministratorName 2\""):
strName+:adminName+ _T(’\’\r\n’)::
int len2 strName. GetLength():
char ~str=new char[len+l];
//CString类型的字符串无法调用\rrite函数写入文本,需要转变成charnt~型;在Unicode编码下(Visual
Stduio环境),无法直接通过强制转换柬将CString变成char*,需要调用WideCharToblultiByte函数转
换,该函数的具体格式可查阅USDN
JideCharTo~lultiByte (CP ACP,0,strName, strName. GetLength(),str, len, NULL, NULL):
str[len]='\O’: //最后一位加入字符串结柬符
inf. TVrite (str, strlen (str)):
delete:lstr;
}
//其他一些配置信息q入
inf. Close():
//关闭配置文件
//创建进程调用secedit,将配置文件导入到组簧略中
PROCESS_INFOIOIATION pi;
STARTUPINFO si;
si.cb=sizeof(STARllPINFO)~.. //进程启动的一些参数配置,略过
//执行的命令
rCw\R corrmand:]2 _TCsecedit /configure /db c:\\czbank.sdb /cfg c:\\czbank.inf /quiet’):
BOOL ret=CreateProcess (NULL, cormand, NLLL, NLLL, FALSE, NOR11AL- PRIORITY CLASS, NULL, NULL,
ksi, &pi): //创建进程执行命令
if(ret){
CloseHandle (pi. hThread): //关闭线程句柄
/fraitForSingleObject (pi. hProcess, INFINITE)://等待进程结束
GetExitCodeProcess (pi. hProcess, &cbrExitCode):
CloseHandle (pi. hProcess): //关闭进程句柄,退出
}
CFile::Remove(_T( "c:\\czbank.inf”)): //删除临时产生的文件
CFile::Remove(_T( "c:\\czbank sdb")):
以上代码在Visual Studi0 2008中测试通过,加同的操作系统是Windows Server 2003。
在MSDN中说对组策略的操作可以通过IGroupPolicyObject接口实现,对应的说明可以在
巾找到,但是关于这个
接口的实际用例以及操作流程网上资料实在太少,我研究了,但未能搞清楚,如果有朋友研
究过这个接口的相关编程。
选自黑防
版权声明:《 windows服务器安全设置 》为王健原创文章,转载请注明出处!
最后编辑:2011-3-23 18:03:16